Table of Contents
- Why Password Security Matters More Than Ever
- Common Password Mistakes You're Probably Making
- The Art of Creating Strong, Memorable Passwords
- Password Managers: Your Digital Vault
- Two-Factor Authentication: Your Second Line of Defense
- Password Recovery Strategies That Don't Compromise Security
- What to Do When Passwords Are Breached
- Password Security for Businesses and Organizations
- The Future of Authentication: Beyond Passwords
- Password Security Checklist
- Advanced Techniques for Security-Conscious Users
- Password Security Myths Debunked
- Teaching Password Security to Others
Why Password Security Matters More Than Ever
In our increasingly digital world, passwords are the keys to our virtual lives. We use them to access everything from email and social media to banking and healthcare portals. Despite the emergence of alternative authentication methods, passwords remain the primary defense against unauthorized access to our sensitive information.
of hacking-related breaches involve compromised credentials, according to Verizon's 2022 Data Breach Investigations Report.
Consider this: the average person has over 100 online accounts, each requiring a password. With so many access points, it's no wonder that password-related breaches account for the majority of hacking-related incidents. The consequences of weak password security can be devastating, ranging from identity theft to financial loss.
Did You Know?
According to Verizon's 2022 Data Breach Investigations Report, 61% of breaches involved credential data. This statistic highlights the critical importance of robust password practices.
The threat landscape is constantly evolving. Cybercriminals employ sophisticated techniques like brute force attacks, dictionary attacks, and phishing schemes to compromise accounts. Understanding these threats is the first step toward building effective defenses.
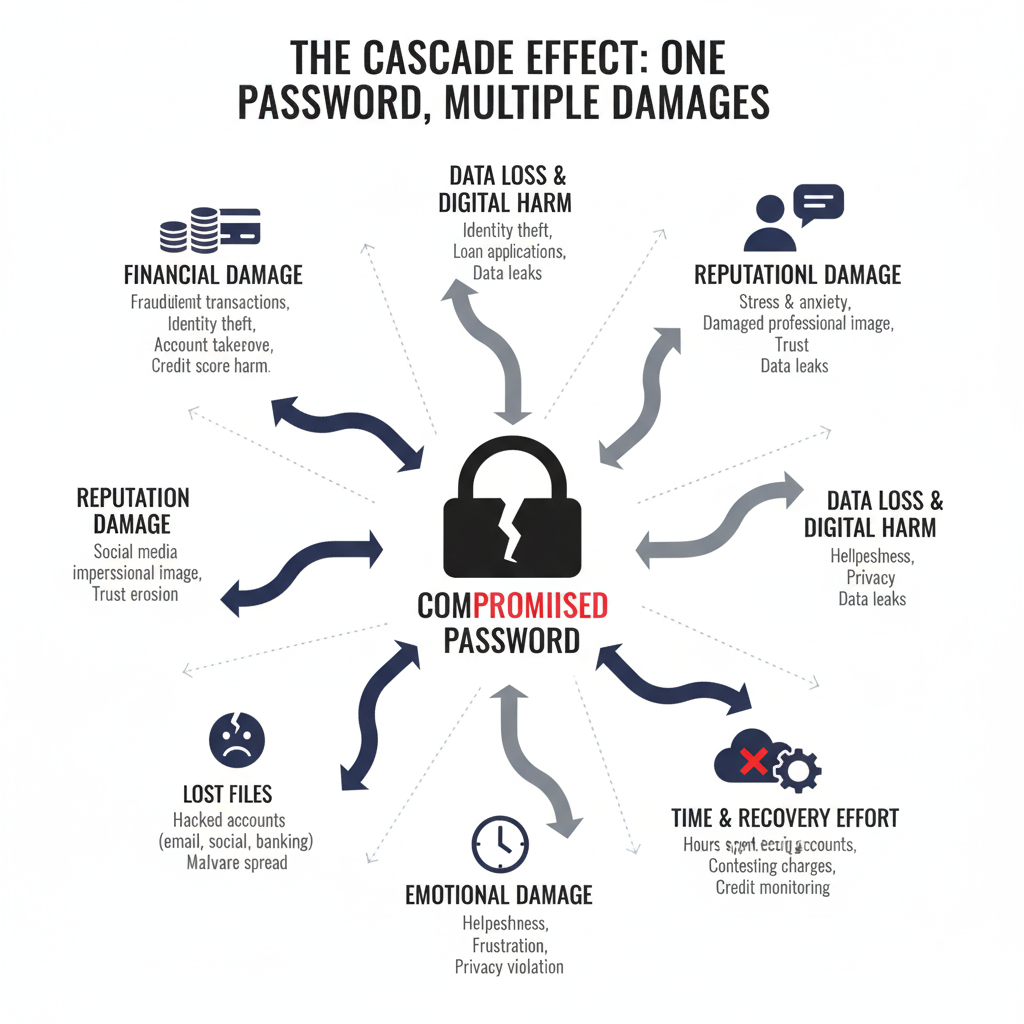
The Real Cost of Weak Passwords
When passwords fail, the repercussions extend far beyond inconvenience. Consider these potential consequences:
- Financial Loss: Hackers can drain bank accounts, make unauthorized purchases, or even take out loans in your name. The average financial loss from identity theft is over $1,000 per incident.
- Identity Theft: With enough personal information, criminals can assume your identity, causing long-term damage to your credit and reputation. Recovery from identity theft takes an average of 6 months and 200 hours of effort.
- Data Breach: A compromised email account can expose sensitive communications and provide access to other connected accounts. Business email compromises alone resulted in over $1.8 billion in losses in 2020.
- Reputational Damage: Hijacked social media accounts can be used to spread misinformation or damage personal and professional relationships.
- Loss of Digital Assets: From cryptocurrency wallets to digital photo collections, weak passwords can lead to permanent loss of valuable digital property.
The Psychology Behind Password Choices
Understanding why people choose weak passwords helps us address the problem more effectively. Several psychological factors contribute to poor password practices:
- Convenience Over Security: The human brain tends to prioritize immediate convenience over long-term security, leading to simple, easy-to-remember passwords.
- Optimism Bias: Many people believe "it won't happen to me," underestimating their risk of being targeted by cybercriminals.
- Password Fatigue: With dozens of accounts to manage, people often resort to recycling passwords or creating simple variations.
- Complexity Confusion: Varying password requirements across different sites lead to frustration and poor password strategies.
The good news is that with proper password hygiene, you can significantly reduce these risks. This guide will walk you through everything you need to know to fortify your digital defenses.
Common Password Mistakes You're Probably Making
Even security-conscious individuals often make critical errors when creating and managing passwords. Let's examine the most common mistakes and why they're so dangerous.
Using Easily Guessable Information
Many people create passwords based on personal information like names, birthdates, or favorite sports teams. The problem? This information is often publicly available on social media profiles, making it easy for attackers to guess.
Password Pitfall
Avoid using any personal information that could be discovered through social engineering or basic research. This includes pet names, anniversary dates, and hometowns.
Password Reuse: The Domino Effect
Using the same password across multiple accounts is like using the same key for your house, car, and office. If one gets compromised, all your accounts become vulnerable. According to a Google survey, 65% of people reuse passwords across multiple sites, dramatically increasing their attack surface.
Simple Patterns and Common Phrases
Passwords like "123456," "password," or "qwerty" remain astonishingly popular year after year. These are the first combinations hackers try when attempting to breach an account. Similarly, common phrases from pop culture or literature are vulnerable to dictionary attacks.
accounts worldwide use "123456" as their password, making it the most common password for the past 5 years.
Infrequent Password Changes
While the conventional wisdom used to recommend changing passwords every 90 days, current guidance from NIST suggests that frequent mandatory changes may actually weaken security by encouraging predictable patterns (like Password1, Password2, etc.). However, this doesn't mean you should never change passwords—especially after a potential compromise.
Writing Down Passwords Insecurely
Jotting down passwords on sticky notes or in unsecured documents creates physical vulnerabilities. If you must keep a written record, it should be stored securely, like in a locked safe.
Sharing Passwords Carelessly
While sometimes necessary, password sharing should be done cautiously and through secure methods. Never send passwords via email or text message, as these can be intercepted or remain in accessible histories.
Underestimating the Threat of Password Spraying
Password spraying is a technique where attackers try a few common passwords against many accounts rather than many passwords against a few accounts. This approach helps them avoid account lockouts and detection. Simple passwords make this attack highly effective.
Now that we've identified the common pitfalls, let's explore how to create strong, secure passwords that are also manageable.
The Art of Creating Strong, Memorable Passwords
Crafting a password that is both secure and memorable might seem challenging, but with the right techniques, it's entirely achievable. Let's explore several effective methods.
The Passphrase Method
Instead of a single word with character substitutions, consider using a passphrase—a sequence of random words that create a mental image. For example: "BlueGiraffeWearsRedHat!" This approach creates longer passwords that are harder to crack but easier to remember.
Pro Tip
Choose unrelated words and include special characters, numbers, and uppercase letters to increase complexity. The more random the word combination, the better.
The Sentence Method
Create a password from the first letters of a memorable sentence. For example, "My first car was a Honda Civic in 2005!" becomes "MfcwaaHCi2005!". This creates a complex password with personal significance.
Avoid Character Substitution Patterns
Simple substitutions like replacing 'o' with '0' or 'e' with '3' are well-known to hackers and their software. If you use substitutions, make them unusual or combine them with other techniques.
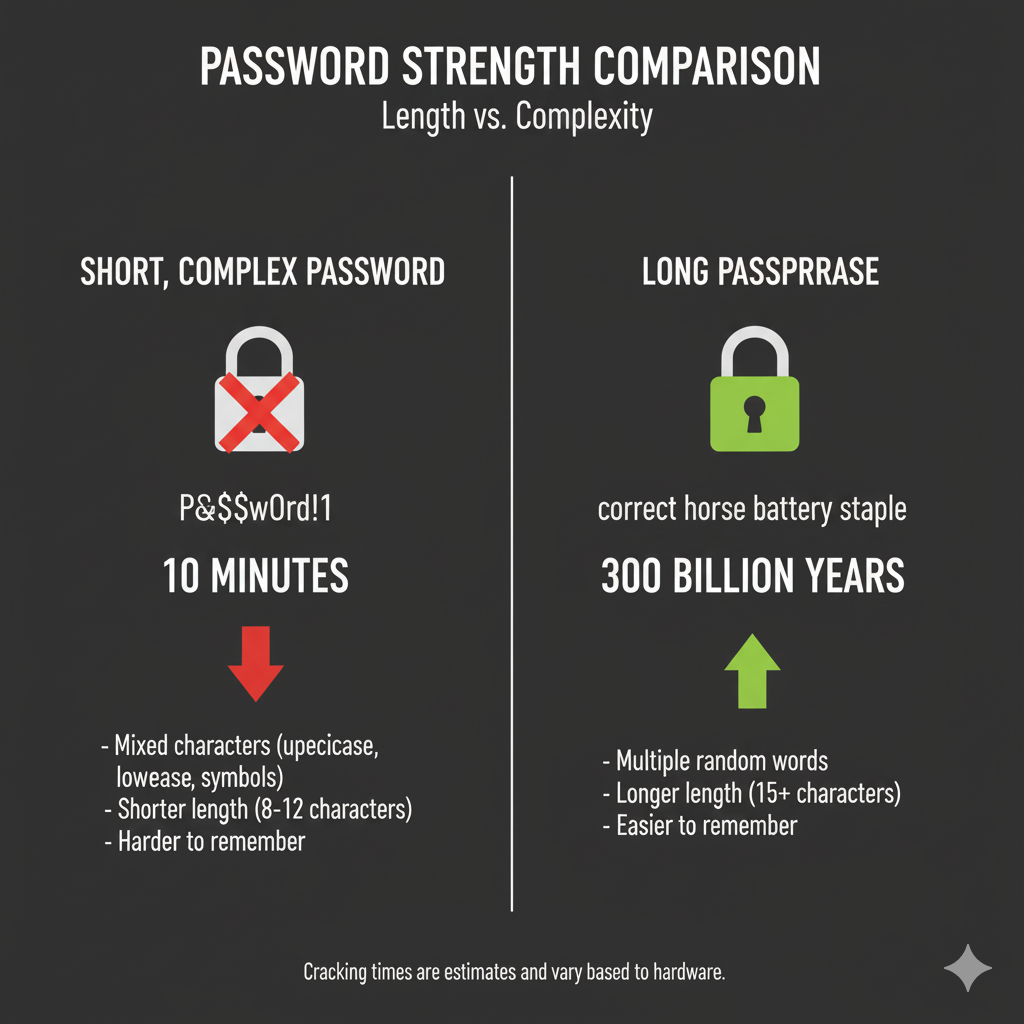
Length Over Complexity
Longer passwords are generally more secure than shorter complex ones. Each additional character exponentially increases the number of possible combinations. Aim for at least 12 characters, with 16 or more for critical accounts.
| Password Type | Example | Time to Crack | Strength Rating |
|---|---|---|---|
| Short & Simple | password123 | Less than 1 second | Very Weak |
| Short & Complex | P@ssw0rd! | 3 hours | Weak |
| Long & Simple | iloveicecream | 3 weeks | Moderate |
| Long & Complex | I-L0v3-Ic3-Cr34m! | 34 years | Strong |
| Passphrase | Blue-Giraffe-Wears-Red-Hat-42! | 5 million years | Very Strong |
Testing Password Strength
How can you know if your password is truly secure? While no online password checker is completely safe (as you're entering your password into a third-party system), you can use estimated strength meters during password creation to get a general idea of robustness.
Remember that the best password is one that is both strong and unique to each account. In the next section, we'll explore how to manage multiple strong passwords effectively.
Password Managers: Your Digital Vault
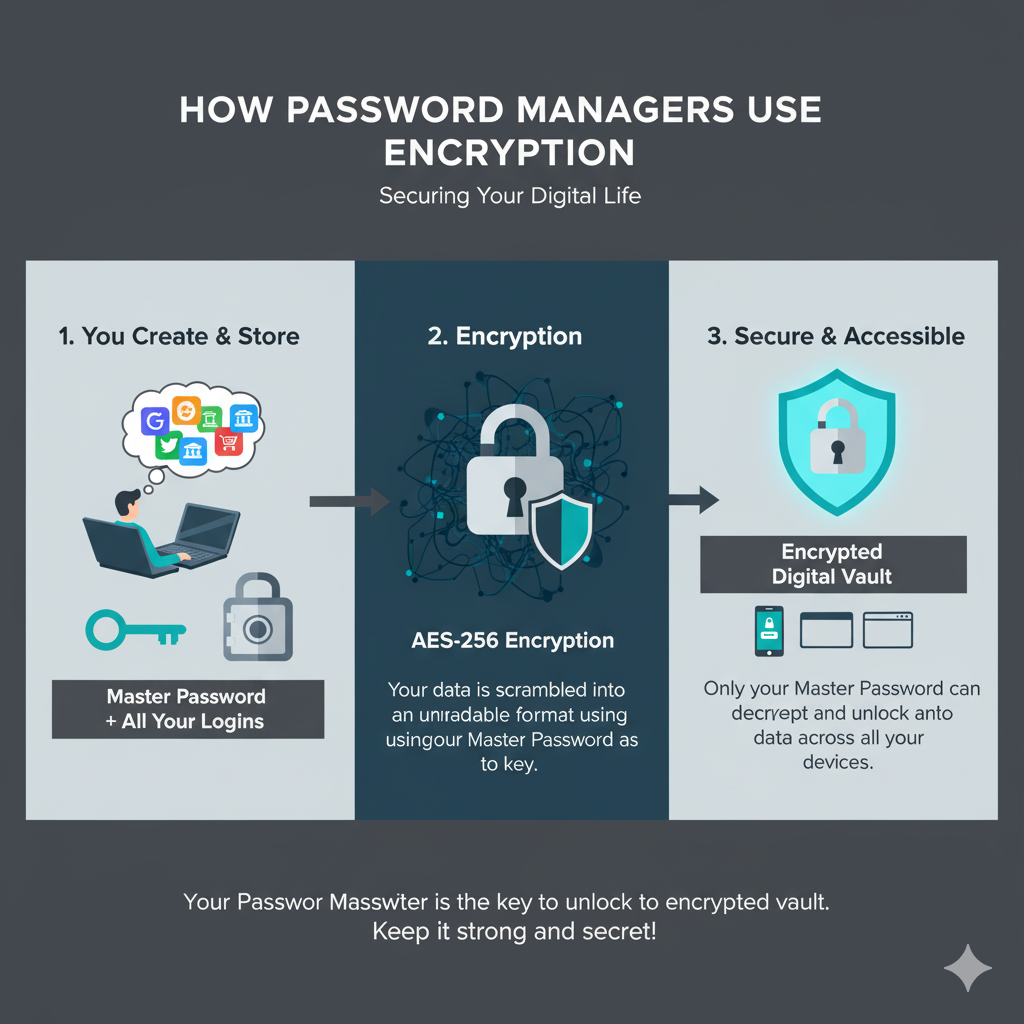
With the need for unique, complex passwords for every account, password managers have become essential tools for modern digital life. These applications securely store all your passwords in an encrypted vault, protected by a single master password.
How Password Managers Work
Password managers encrypt your password database with a master password—the only one you need to remember. The encrypted data is either stored locally on your device or in the cloud, depending on the service. Most password managers include features like:
- Password generation
- Auto-fill capabilities
- Security alerts for compromised passwords
- Secure password sharing
- Digital wallet functionality
- Secure notes for other sensitive information
- Dark web monitoring for your credentials
Choosing a Password Manager
When selecting a password manager, consider these factors:
- Security: Look for zero-knowledge architecture, meaning the provider cannot access your data. End-to-end encryption is essential.
- Cross-platform compatibility: Ensure it works on all your devices and browsers. Mobile apps with biometric unlock are particularly convenient.
- Features: Evaluate additional features like secure notes, identity monitoring, or emergency access.
- Price: While many offer free versions, paid plans often provide enhanced security features and syncing across multiple devices.
- Reputation: Choose a provider with a long track record of security and transparency.
Popular Password Managers
Some widely trusted options include Bitwarden (open-source and affordable), LastPass (feature-rich), 1Password (excellent user experience), and Dashlane (premium features). Each has strengths and weaknesses, so research which best fits your needs.
Master Password Considerations
Your master password is the key to your digital kingdom, so it needs to be exceptionally strong yet memorable. Use the passphrase method discussed earlier, and consider adding uncommon punctuation or character substitutions that only you would remember.
Critical Security Note
If you forget your master password, most password managers cannot recover it due to their zero-knowledge architecture. Make sure you remember it or store it in an extremely secure location.
Transitioning to a Password Manager
Moving to a password manager can seem daunting, but the process is straightforward:
While password managers significantly enhance security, they should be complemented with additional protection layers, which we'll explore next.
Password Security Checklist
Implement these practices to significantly enhance your password security:
- ✅ Use unique passwords for every account
- ✅ Create passwords with at least 12 characters
- ✅ Enable two-factor authentication wherever available
- ✅ /Use a reputable password manager
- ✅ Regularly review account security settings
- ✅ Check for breached passwords using trusted services
- ✅ Update recovery information regularly
- ✅ Educate family members about password security
- ✅ Use passphrases instead of complex short passwords
- ✅ Avoid password hints that others could guess
- ✅ Change default passwords on devices and routers
- ✅ Be cautious of phishing attempts asking for credentials
Password security is not a one-time task but an ongoing practice. By implementing the strategies outlined in this guide, you'll significantly reduce your risk of falling victim to account compromise and identity theft.
Stay Vigilant
The digital landscape evolves constantly, and so do cyber threats. Stay informed about new security developments and continue refining your password practices.

Advanced Techniques for Security-Conscious Users
For those who want to take their password security to the next level, consider these advanced techniques:
Hardware Security Keys
Physical security keys like YubiKey or Google Titan provide the strongest form of two-factor authentication. They're resistant to phishing and can't be duplicated remotely.
Password Salting
Create a system where you add a unique "salt" to each password. For example, your base password might be "BlueGiraffe!" but for Amazon, you add "Amz" to make "BlueGiraffe!Amz".
/*Regu*lar Security Audits
Conduct quarterly reviews of your password hygiene, checking for reused passwords, updating older passwords, and ensuring all accounts have 2FA enabled.
Breach Monitoring Services
Use services like Have I Been Pwned to monitor if your email appears in data breaches, alerting you to change affected passwords immediately.
Password Security Myths Debunked
Let's clear up some common misconceptions about password security:
Myth 1: Changing Passwords Frequently Improves Security
Recent guidelines from NIST suggest that frequent password changes may actually decrease security by encouraging predictable patterns.
Myth 2: Complexity Is More Important Than Length
Length is actually more important than complexity. A long passphrase is stronger than a short complex password.
Myth 3: Password Managers Are Less Secure
Reputable password managers use strong encryption and are generally more secure than the alternatives (password reuse or weak passwords).